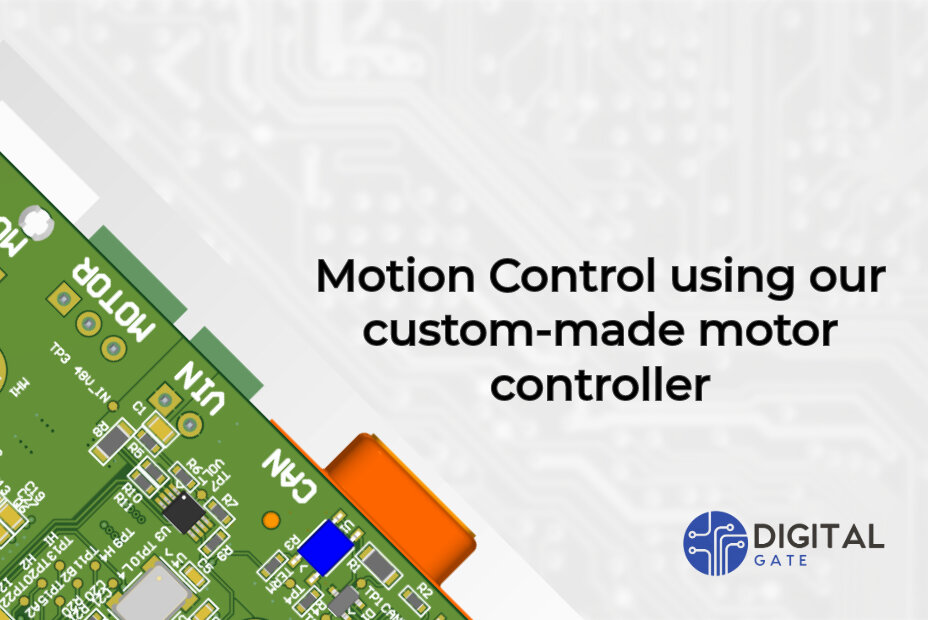
Optimizing our Custom Motor Controller for Motion Control
Using our carefully designed board, we demonstrate the impressive power and flexibility of integrating modern technologies into motor controllers. In the realm of small to

Using our carefully designed board, we demonstrate the impressive power and flexibility of integrating modern technologies into motor controllers. In the realm of small to
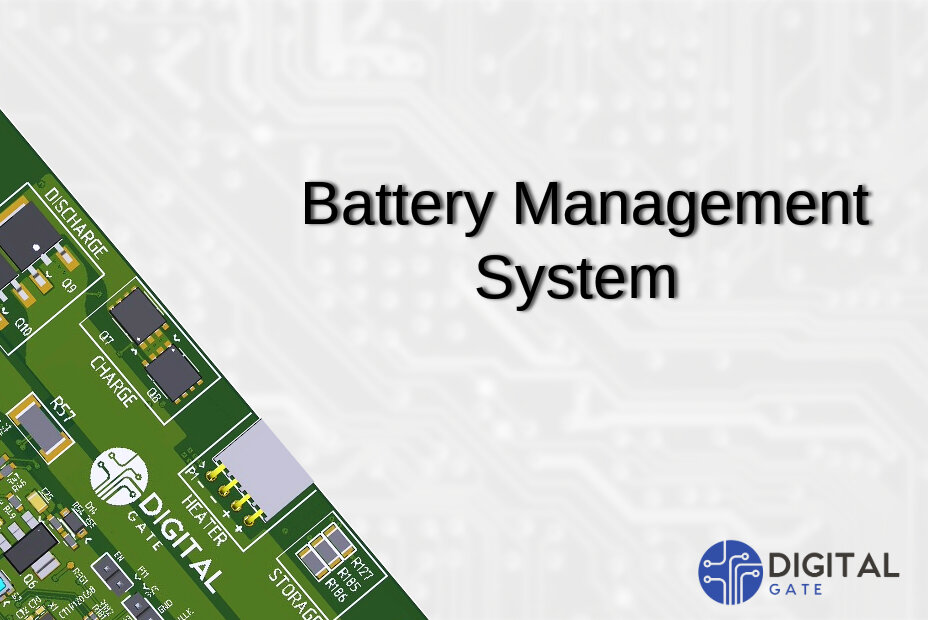
Digital Gate is excited to introduce you to one of our flagship products: an efficient and secure Battery Management System (BMS), meticulously designed and implemented

DigitalGate is excited to announce its forthcoming participation at Embedded World 2024 taking place in Nuremberg from the 9th to the 11th of April. Come,

Is the capacitance of the capacitor always same? Multilayer ceramic capacitors (MLCCs) offer several advantages that make them a popular choice for various electronic applications,

C++ 20 and 23 have a lot of new features which can reduce boilerplate code, increase efficiency and make the code drastically more readable. Not

DigitalGate is excited to announce its participation at the Embedded World 2023 organized in Nuremberg between 14.03 and 16.03. Come, and meet us at our

What is it? Type erasure is the technique used to hide the type meta-data of some data. When we store and manage data in such

Considering the current developments in the global market, especially having the issue of a Global Chip Shortage, there are some issues to be addressed when

A command-line utility by the name of DevTool serves as the foundation of the extensible SDK. With the help of this tool, you may create,